Organizations Must Be Ready to Handle a Cybersecurity Incident
We live in a digital world, and while digitization has made collaboration easier, it has also led to the expansion of the cybersecurity threat landscape. To keep enterprise data secure, organizations need to develop a robust cybersecurity program that helps them remain vigilant.
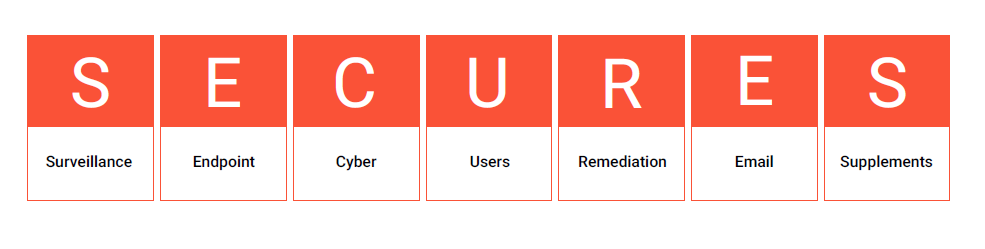
Safeguard Your Data with Synoptek’s SECURES Model
As a Global Systems Integrator and Managed Services Provider, Synoptek provides tailor-made service offerings to its clients depending on where they lie on Synoptek’s Capability Maturity Model through a comprehensive set of assessments. Using this model as a foundation, we have developed the Synoptek SECURES Maturity Model which allows us to assess the security controls our clients currently have in place and suggest additional ones to safeguard their growing business against evolving threats and breaches.
Developed based on several interviews conducted internally and externally and through constant listening and learning, Synoptek’s SECURES Model allows you to build a strong foundation of security while enabling you to gradually integrate additional services and protections. It has seven domains and comprises over 34 high-level controls, which every organization needs, to be truly secure.

White Paper
Synoptek SECURES Maturity Model