What comes to your mind when you hear the word ‘cost’ as a healthcare organization? Perhaps you are always in search of a successful cost optimization strategy. More than any other industry today, healthcare finance leaders feel more burdened by the pressure to reduce costs.
Rising labor and supply costs are causing healthcare organizations to consider cost-reduction opportunities. Managed IT services for healthcare optimize costs by streamlining operations, mitigating risks, and transforming unpredictable IT expenses into predictable, controlled outlays, freeing up resources for core business processes.
Evaluating the Cost Benefits of Managed Services in Healthcare
According to a Precedence research report, the global managed IT services market for healthcare is projected to surpass $184.82 billion by 2033. Healthcare IT managed services are an affordable, risk-managed, and technologically agile approach that enhances overall revenue.
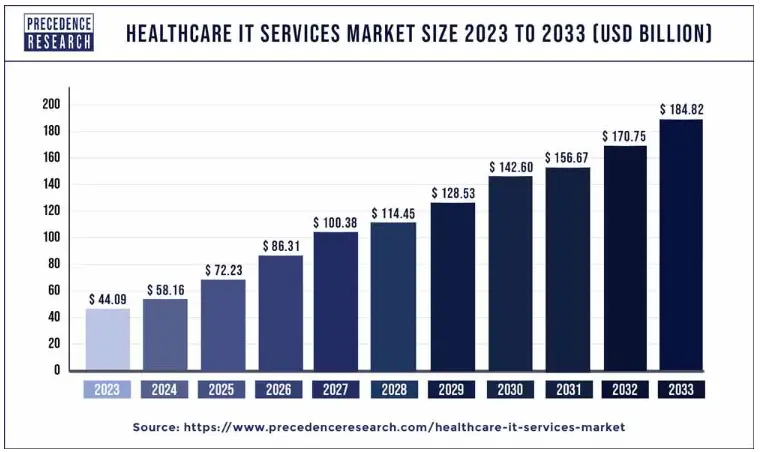
Source: Precedence Research
Key factors driving the managed services market growth include increasing dependence on IT operations, new applications to improve business productivity, and the need for specialized managed service providers (MSPs) to manage complex IT infrastructure and reduce IT staffing costs.
Here’s how to evaluate the cost benefits:
Outsourcing Non-core Functions
Healthcare providers can outsource non-core IT functions like network management, data backup, and help desk support to experienced managed services providers. By outsourcing to an MSP, healthcare providers can avoid the capital expenses of acquiring and maintaining equipment like servers and workstations. This allows them to:
- Reduce capital expenditure on IT infrastructure and staffing needs.
- Focus internal resources on core clinical and patient care activities.
- Access specialized IT expertise and capabilities that they may lack in-house.
Scalability and Flexibility
Managed service providers offer healthcare organizations the ability to easily scale IT resources up and down as required. This flexibility helps to:
- Accommodate fluctuations in patient volume and staffing.
- Rapidly deploy new technologies and capabilities.
- Manage costs more efficiently by only paying for the services required.
Predictable Costs and Budgeting
Healthcare companies sometimes incur unpredictable and hefty costs from sudden IT crises. Managed services are offered at fixed monthly subscription rates, making IT costs more predictable. This allows them to:
- Plan for IT expenses accurately.
- Avoid the unpredictable costs of maintaining in-house IT infrastructure.
- Free up capital for strategic investments in patient care.
Enhanced Security and Compliance
In addition to the hard costs mentioned above, managed services can reduce soft costs like lost productivity due to downtime, reputational damage from ransomware attacks, and penalties associated with HIPAA compliance violations.
MSPs help healthcare organizations avoid these costly consequences by ensuring reliable, secure IT operations. They also offer robust security measures and ensure compliance with regulations like HIPAA. This enables healthcare organizations to:
- Protect sensitive patient data and avoid costly data breaches.
- Meet complex regulatory requirements more effectively.
- Minimize the risk of penalties and reputational harm.
Ultimately, IT managed services for healthcare offer an affordable, risk-managed, and technologically agile approach that optimizes operational efficiency and boosts overall revenue. For healthcare providers looking to reduce costs while enhancing patient care, partnering with the right MSP is a financially intelligent decision.
Leveraging Managed Services for Cost Optimization
Leveraging healthcare managed services for cost optimization allows organizations to reduce IT expenses by outsourcing infrastructure management, maintenance, and support. This approach enables access to cutting-edge technology and expertise without high in-house development costs, improving efficiency and significant savings. Here are some areas healthcare organizations must explore for effective and sustained cost optimization:
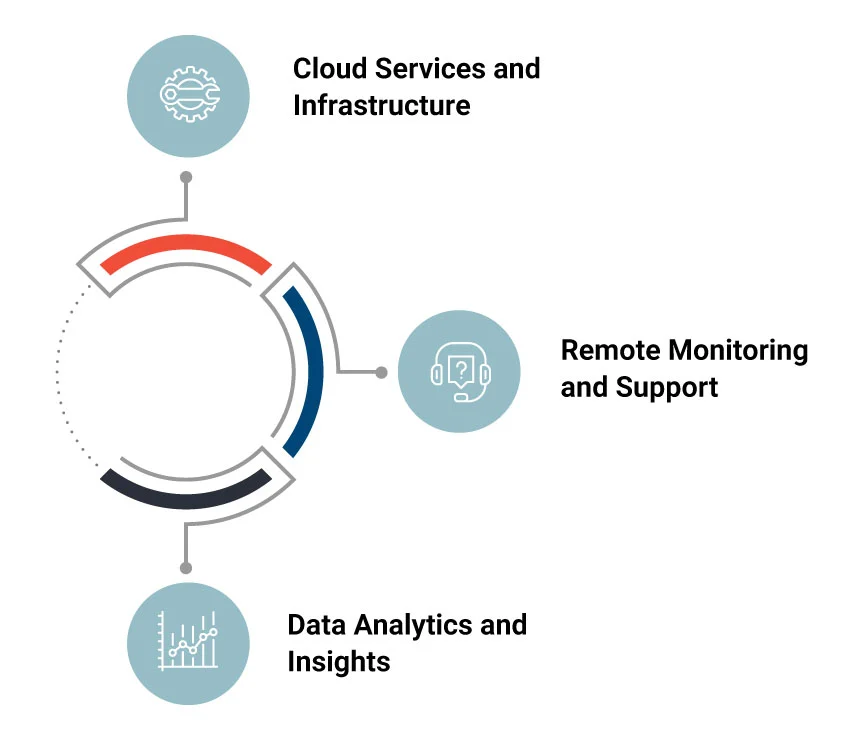
Cloud Services and Infrastructure
Cloud computing offers healthcare organizations a cost-effective alternative to on-premises infrastructure. By outsourcing IT infrastructure to cloud providers, hospitals and practices can:
- Avoid the capital expenses of acquiring and maintaining servers, storage, and networking equipment.
- Scale resources up or down as needed to accommodate fluctuations in demand.
- Shift from CapEx to OpEx models, ensuring more predictable monthly costs.
Cloud services also enable healthcare providers to rapidly deploy new applications and capabilities without the overhead of managing underlying infrastructure. This agility helps drive operational efficiency and additional cost savings.
Remote Monitoring and Support
Managed IT services providers offer 24/7 remote monitoring and proactive maintenance to prevent issues before they impact operations. By continuously monitoring systems and applying updates, healthcare organizations can:
- Identify and resolve problems quickly before they escalate into costly downtime.
- Ensure systems are running at optimal performance to maximize efficiency.
- Reduce the need for on-site support and emergency break-fixes.
Proactive maintenance also extends the useful life of technology assets, deferring the need for costly hardware refreshes. This helps healthcare organizations optimize their technology investments.
Data Analytics and Insights
Managed service providers (MSP) collect and analyze vast amounts of operational data to uncover cost optimization opportunities. By leveraging advanced analytics and machine learning, healthcare institutions can:
- Identify inefficient processes, resource utilization patterns, and cost drivers.
- Get data-driven recommendations for optimizing workflows and reducing waste.
- Enable predictive maintenance to avoid equipment failures and downtime.
By strategically leveraging cloud services, remote support, and data analytics, healthcare providers can harness the power of managed technology to significantly reduce costs while enhancing operational efficiency and patient care quality.
6 Tips on How to Choose Healthcare Managed Service Providers
Evaluating and choosing your healthcare managed IT services provider can be a make-or-break decision. Here are six tips to keep in mind while partnering with a Managed Healthcare Provider:
Healthcare IT Experience and Expertise
Look for an MSP with extensive experience working with healthcare organizations. They should deeply understand your specific IT needs, compliance requirements like HIPAA, and the ability to support critical clinical workflows.
Large Pool of Certified Resources
Ensure your chosen MSP has access to a vast network of highly skilled and certified healthcare IT professionals. They should be able to quickly scale up to meet your staffing needs, whether for routine support or specialized projects. Extra brownie points if they can proactively plan for your future IT infrastructure needs.
Collaboration and Customization
Choose an experienced MSP who will work closely with you to understand your specific healthcare workflows, needs, goals, and pain points. Opt for a partner who can tailor their services and solutions to meet your specific requirements.
Communication and Customer Service
Timely, responsive, and clear communication sets the tone for the success of any project. Choose an MSP that prioritizes transparency and clear communication. They should have a track record of providing exceptional customer service and employee support.
Robust Security, Backup, and Business Continuity
Robust data backup, disaster recovery, and cybersecurity measures are essential. Ensure your MSP provides comprehensive security solutions with daily automatic backups to secure and remote servers. They should also have a solid disaster recovery plan to protect sensitive patient data and minimize downtime during an outage or attack.
Ongoing and Proactive Support
Select an MSP who can provide 24/7 monitoring, maintenance, and proactive issue resolution to keep your systems running smoothly. Duly check for a track record of fast response times and effective problem-solving capabilities.
Curb the Cost Complexity in Your Care Delivery with a Trusted Healthcare MSP
In conclusion, adopting managed IT services in healthcare offers a strategic pathway to enhance cost efficiency while maintaining high standards of care. By outsourcing IT infrastructure management, you can focus on the core mission of patient care, reduce operational costs, and gain access to the latest technological advancements.
This approach streamlines administrative processes and ensures data security, enabling scalability and flexibility in adapting to future technological innovations. If you’re looking to drive sustainable growth and operational excellence, head here.
If you want managed services in Irvine, you can contact our experts here.