

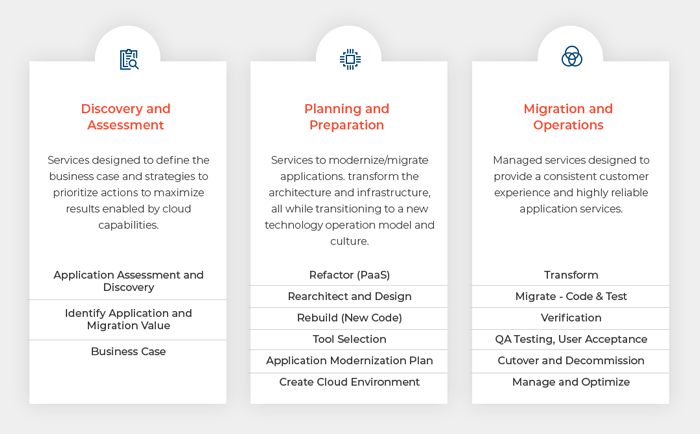
Cloud migration consulting is critical for planning and strategy. It involves assessing the current IT landscape, identifying migration goals, analyzing risks, defining architecture, and creating a roadmap. Consultants guide your organization through the entire cloud migration lifecycle, ensuring maximum ROI while avoiding common pitfalls.
Are you looking to engage with a cloud migration services provider? As experienced cloud migration companies, we offer comprehensive assessment, planning, and implementation services to ensure a smooth transition to the cloud. Contact our cloud migration experts to learn more about how we can support your organization's journey to the cloud.
Cybersecurity is a collection of methodologies, technologies, and processes used to safeguard an organization’s computer systems, networks, and data from cyberattacks or unauthorized access. The primary motive of cybersecurity is to shield all corporate assets from external and internal threats, as well as from natural disasters.
Cybersecurity systems detect, examine, and fix potential system weaknesses and vulnerabilities before hackers or malicious software exploit them. An organization, its employees, and the processes and technologies must come together to create a solid cybersecurity layer that protects it from potential attacks.
In today's tech-driven world, the increasing accessibility of sensitive information online emphasizes the need for robust cybersecurity measures. Frequent high-profile breaches highlight the financial and reputational damage cyberattacks can inflict. As cyber threats continue to surge, businesses of all sizes are extremely vulnerable to attacks.
In the world of cybersecurity, there are several key areas that help keep IT infrastructure safe. These include application, cloud, data, mobile, and network security. Let's take a brief look at each to understand their roles in keeping businesses protected online.
Application security refers to the practices, procedures, and strategies used to protect web and mobile applications against security threats and vulnerabilities. These threats can include malicious activities such as unauthorized access, data breaches, injection attacks (such as SQL injection), denial of service (DoS) attacks, and more.
Cloud security refers to a set of policies, technologies, practices, and controls designed to protect data, applications, and infrastructure stored and processed in cloud computing environments. This specialized field of cybersecurity focuses on protecting cloud-based assets from multiple threats, including unauthorized access, data breaches, data loss, and service disruptions.
Data security involves safeguarding digital information throughout its entire lifecycle to prevent corruption, theft, or unauthorized access. This comprehensive approach encompasses hardware, software, storage devices, user devices, access controls, administrative measures, and organizational policies and protocols.
Mobile security refers to a set of practices, initiatives, and technologies designed to protect mobile devices (such as smartphones, tablets, and laptops) and the information stored or transmitted on them from various security threats, including spam, phishing, ransomware, theft, misuse, etc.
Network security refers to the practices, measures, and technologies put in place to protect computer networks and the data transmitted over them from various security threats and unauthorized access. Network security involves implementing safeguards such as firewalls, intrusion detection systems, encryption, access controls, and regular monitoring to detect and mitigate cyber threats.
No, cybersecurity and information security are not the same thing, although they are closely related. Information security primarily focuses on safeguarding data from unauthorized access or manipulation. Cybersecurity, on the other hand, is a broader field that encompasses all aspects of security, including protecting devices, networks, and systems from cyber threats. This goes beyond data and includes protecting entire digital ecosystems. While they have distinct focuses, both information security and cybersecurity work together to ensure that an organization and its data are secure and that its digital infrastructure is resilient to cyber-attacks.
Attackers are constantly threatening the digital assets of your company. Therefore, there is a continuous need to protect them. Here are the top reasons why IT security is vital to your business:
As businesses get increasingly digital, cybercrime has only found new ways to deepen its grip.
Listed below are the most significant types of cybersecurity attacks in the current times:
Synoptek’s Cybersecurity Services will increase your IT team’s ability to safeguard applications, computing, and network infrastructure with modern security solutions that are fully managed, simple to adopt, and do not require substantial upfront investments. Synoptek’s Managed Cybersecurity Services are updated regularly, allowing businesses to cope with new threats in a competent and timely manner.
Our cybersecurity experts have the capacity to reverse-engineer malware and other suspect applications to extract vital information that can be utilized to create new security content that will safeguard the entire client base from future breaches. When it comes to cybersecurity, Synoptek has the following offerings:
To know more about Synoptek’s Cybersecurity framework, please click here.
Artificial Intelligence (AI) is a system that can demonstrate human intelligence capabilities like reasoning and learning. This ability to simulate human comprehension aids problem-solving and decision-making.
Generative AI (GenAI) is a subset of artificial intelligence. It leverages large language models (LLMs) to create new content, including texts, images, audio, and videos. Trained on vast amounts of data, it can generate outputs that resemble human-created content without directly copying the original data.
Humans can use generative AI tools for chatbots, image synthesis, music composition, and code generation applications.
Generative AI tools use existing information to create new data according to human prompts. For example, developers can provide a generative AI system with a prompt that enables the system to offer code suggestions.
Predictive AI systems use past or present data to forecast what could happen in the future. For example, financial institutions can use predictive AI models to predict market trends and stock prices based on emerging economic factors.
Generative AI relies on advanced machine learning techniques, such as deep learning and neural networks, to analyze data patterns and generate relevant outputs.
It uses architectures like transformers (e.g., GPT models), diffusion models (for image generation), GANs (Generative Adversarial Networks), and VAEs (Variational Autoencoders) to produce high-quality content.
The model generates responses based on user prompts, continually refining its outputs through iterative learning and fine-tuning.
Examples of generative AI are many, with use cases such as:
The advantages of generative AI tools are many for businesses across industries, such as:
Generative AI tools offer many benefits, but organizations must also know about generative AI implementation risks. These include:
The field of decision intelligence blends business intelligence (BI) and artificial intelligence (AI) to improve organizations' decision-making processes. With Decision Intelligence, business decisions can be made more quickly, accurately, and consistently, leveraging a host of advanced predictive models.
The purpose of Decision Intelligence is to assist businesses in identifying opportunities, developing strategies, making plans, launching projects, and predicting results. Decision Intelligence models enable companies to maximize their efforts by providing valuable insights into business operations.
Platforms offering Decision Intelligence facilitate decision-making and provide insights, recommendations, and context, enabling organizations to realize better value from technology investments. A few of the key benefits include the following:
Decision Intelligence is considered the biggest B2B movement of this generation. Decision Intelligence is AI with a purpose that leads to growth, efficiency, profit, and sustainability. To get started with Decision Intelligence, you need:
Using Decision Intelligence, users can identify patterns, and connections, to find the best solution to all unforeseen circumstances.
Synoptek understands that each organization has specific needs when it comes to data. Therefore, we tailor our insights services to help our clients meet their goals.
Whether you are at the very start of your data insights journey or are trying to transition to the next stage, Synoptek can help you translate your goals into an actionable roadmap.
In the realm of data insights, Synoptek offers the following services:
To learn more about Synoptek’s Data Insights offering, please click here. To speak with a Decision Intelligence consultant, contact us today.
Help Desk and Technical Support refers to the services provided by IT professionals to assist users with IT-related problems, software issues, and other technical difficulties. This support can range from basic troubleshooting to complex problem-solving and is typically organized into different tiers based on the level of expertise required.
While the terms are often used interchangeably, there are some distinctions:
In practice, many organizations integrate both functions, with the 24/7 IT help desk serving as the initial point of contact before escalating to more specialized technical support team when necessary.
Helpdesk support services teams are equipped to handle a wide range of technical and IT-related issues that users may encounter in their daily work. Some common areas of support include:
A 24/7 IT help desk ensures that these issues can be addressed anytime, providing users with continuous access to support.
Implementing a robust 24/7 IT Help Desk and Technical Support system offers numerous advantages to an organization. Key benefits include:
With helpdesk support services, organizations can further reduce downtime and ensure uninterrupted support.
Are you looking for professional IT Helpdesk Services in Orange County? Our team of experienced IT professionals offers comprehensive support solutions tailored to your specific needs. Contact us to learn how we can help improve your user support experience and boost overall IT efficiency.
IT infrastructure assessment comprehensively evaluates an organization’s existing IT infrastructure, including servers, networks, storage systems, software, and security protocols. The goal is to identify current capabilities, uncover vulnerabilities, ensure alignment with business goals, and create a roadmap for transformation.
Conducting a comprehensive IT infrastructure optimization can deliver a variety of strategic and operational advantages:
Organizations should consider an IT infrastructure assessment during the following:
An IT infrastructure assessment is critical in strengthening IT security by identifying unmanaged assets, outdated software, misconfigured systems, and potential entry points for cyber-attacks.
The assessment often results in recommendations that include enhanced firewalls, updated antivirus solutions, role-based access controls, and other security best practices aligned with compliance standards identified through a comprehensive IT infrastructure audit.
IT infrastructure optimization is a critical first step in determining cloud readiness. It evaluates existing workloads, hardware compatibility, network capacity, and data sensitivity, helping organizations plan successful cloud migrations. IT infrastructure consulting teams often use the assessment phase to develop customized cloud strategies based on organizational needs.
IT infrastructure assessment services can benefit organizations across all sectors—healthcare, finance, education, manufacturing, and professional services. These evaluations are beneficial for mid-size to large enterprises with complex systems or growing compliance obligations. IT infrastructure consulting firms often tailor assessments to specific industry standards and business models.
A comprehensive IT infrastructure assessment typically includes:
Many regulatory standards require secure, reliable tech environments. An IT infrastructure optimization activity helps identify areas where systems may fall short—such as data encryption, user access controls, backup practices, or software patch management. When conducted by specialized IT infrastructure consulting providers, these assessments help ensure compliance with HIPAA, PCI-DSS, and SOC 2 standards through comprehensive IT infrastructure audits.
IT infrastructure assessments help address these common challenges:
IT infrastructure consulting firms bring expertise and industry best practices to the assessment process. They conduct in-depth evaluations, interpret complex IT data, and develop actionable strategies. As experienced technology partners, consultants ensure recommendations align with current infrastructure realities and long-term business goals—including improved risk management and IT infrastructure optimization.
Are you thinking about optimizing your technology environment? Start with a comprehensive Infrastructure Assessment. Our expert infrastructure consulting team provides end-to-end evaluation services to help you maximize performance, reduce risk, and plan. Contact us today to discuss your IT infrastructure needs.
24/7 helpdesk monitoring and support is an around-the-clock support model that helps businesses or individual users with technical assistance for monitoring IT systems or resolving user issues. A 24/7 IT helpdesk ensures that users can access support anytime, regardless of the hour or day, including nights, weekends, and holidays.
A 24/7 IT helpdesk allows users to get help and find answers to IT-related queries almost immediately. Companies offering 24/7 helpdesk support services often do this via:
24/7 helpdesk support services ensure users get access to support anytime, including nights, weekends, and holidays. An IT helpdesk support company offering 24/7 IT support services helps:
While looking for an IT helpdesk support company, there are several aspects to look for:
Are you looking for professional IT helpdesk services in Orange County? As an award-winning, top-ranked technology consulting and managed service provider (MSP) in Orange County, we offer a range of 24/7 IT Support and Maintenance Services. Contact our helpdesk support services experts in Orange County to know more.

Virtual CIO (vCIO) services provide strategic IT leadership and consulting to businesses, typically small and medium-sized enterprises (SMEs), by a remote, part-time Chief Information Officer. vCIOs offer executive-level expertise in aligning technology with business goals, optimizing IT investments, and driving operational efficiency.
Unlike a full-time, in-house CIO, a virtual CIO operates as an independent contractor or through a managed service provider (MSP). This model offers more flexibility and cost-effectiveness, as businesses can access high-level IT strategy without the financial burden of a permanent executive-level position.
Engaging a virtual chief information officer, typically through a managed services provider, can deliver several benefits to businesses, including:
vCIO (Virtual Chief Information Officer) services provide strategic IT leadership and consulting tailored to various industries. Here are the key sectors that benefit most from these services:
Are you looking to engage with a virtual CIO in Orange County? As an award-winning, globally trusted technology consulting and managed service provider (MSP) in Orange County, we offer a comprehensive range of virtual CIO services. Contact our vCIO experts in Orange County to learn more.